42 security labels access control
Label-based access control (LBAC) overview - IBM A security administrator allows users access to protected data by granting them security labels. When a user tries to access protected data, that user's ... Access control - Wikipedia WebIn the fields of physical security and information security, access control (AC) is the selective restriction of access to a place or other resource, while access management describes the process.The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization.. Locks and login credentials are …
Access control for folders with IAM - Google Cloud Web19.09.2022 · IAM lets you control who (users) has what access (roles) to which resources by setting IAM policies. IAM policies grant specific role(s) to a user giving the user certain permissions. This page explains the IAM roles that are available at the Folders level, and how to create and manage IAM policies for folders using the Resource Manager API.
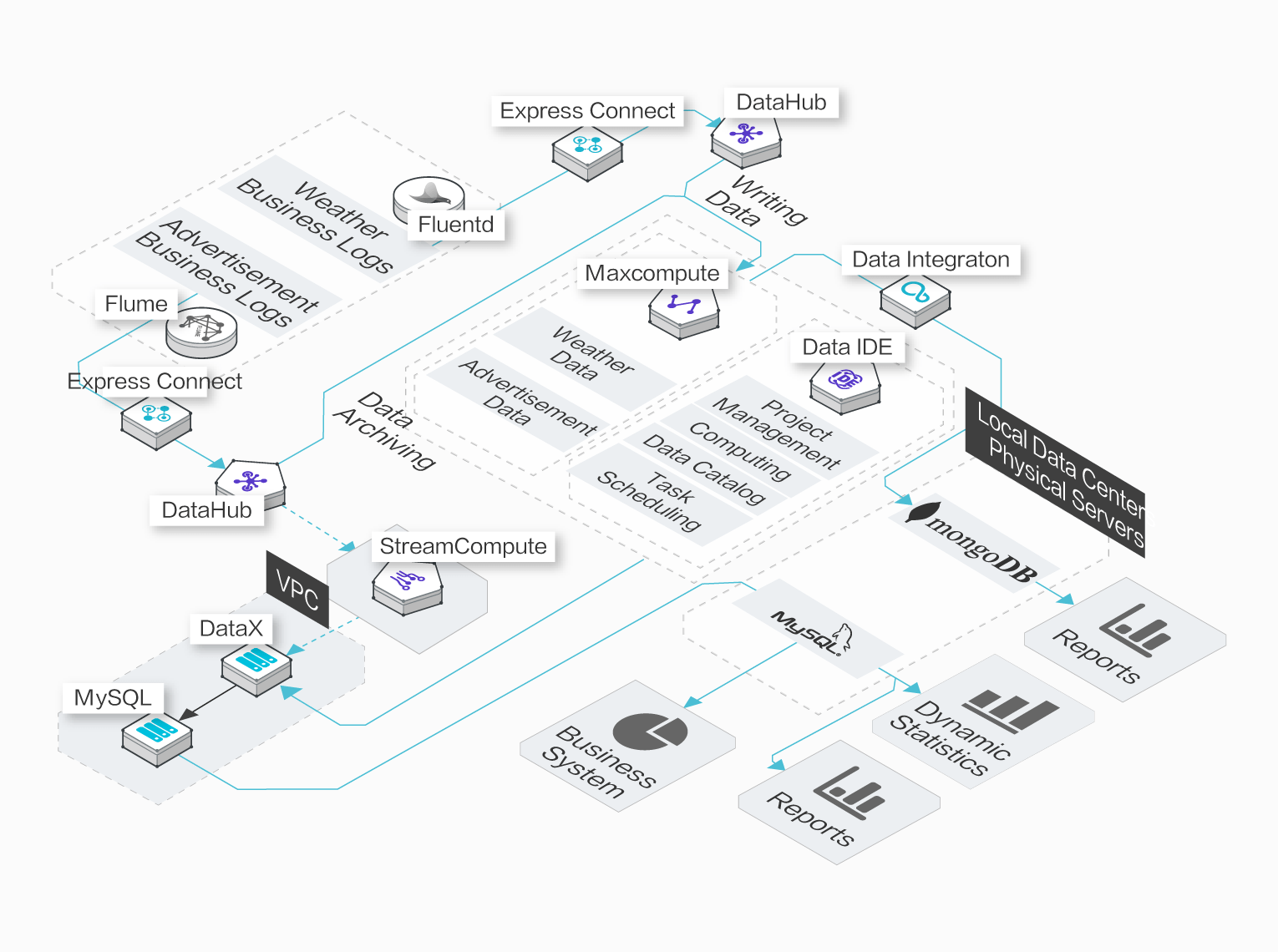
Security labels access control
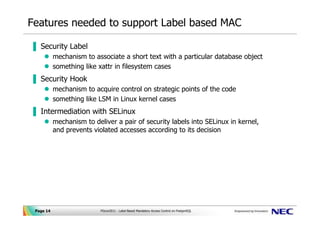
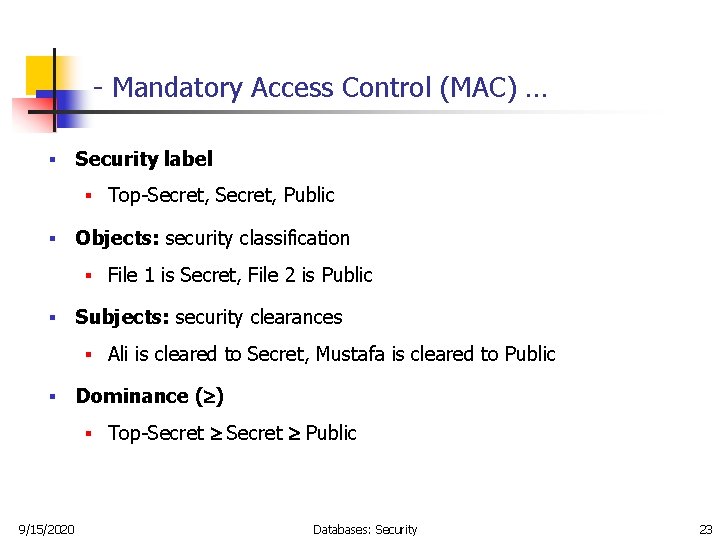
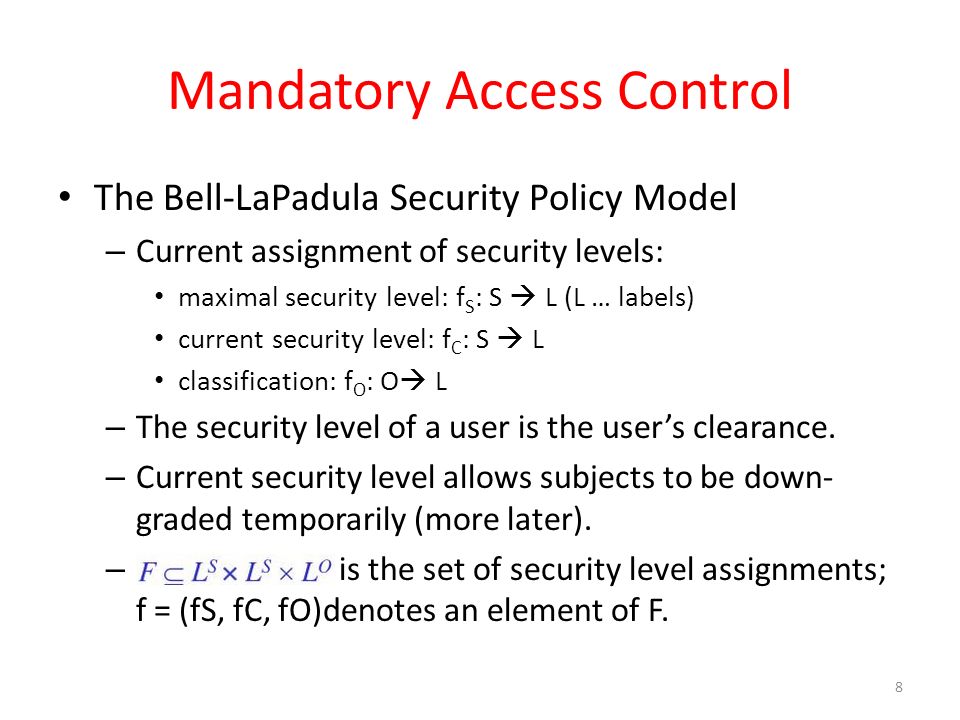
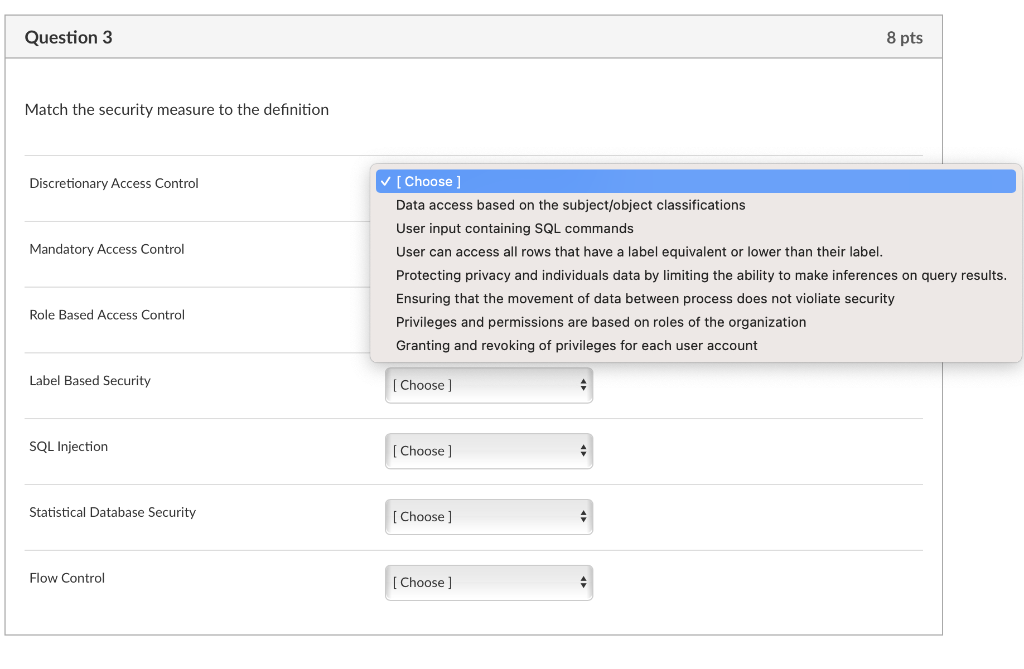
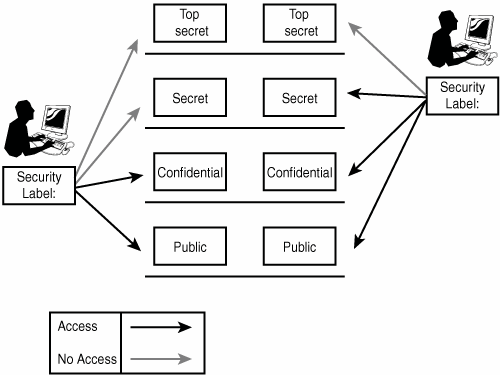
Mandatory Access Control: How does it work? - IONOS Oct 14, 2020 · There are a number of options available for implementing and maintaining access control, including Mandatory Access Control. This model is also used in the political and military branches, which require tamper-proof protection of data. Keep reading to find out how this rule-based access control works and what its pros and cons are. Mandatory Access Control - an overview | ScienceDirect Topics Mandatory Access Control ( MAC) is system-enforced access control based on subject's clearance and object's labels. Subjects and objects have clearances and labels, respectively, such as confidential, secret, and top secret. A subject may access an object only if the subject's clearance is equal to or greater than the object's label. How security labels control access - IBM Security labels rely on security label components to store information about the classification of data and about which users have access authority.
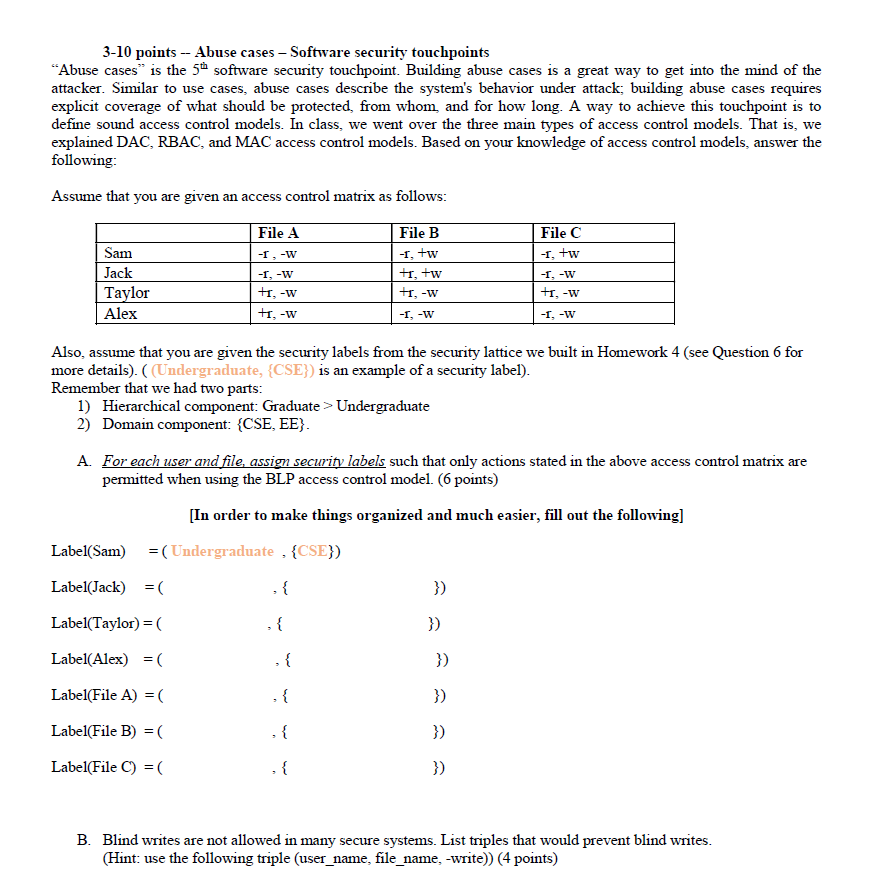
Security labels access control. Define access control list and capability list and compare them ... An access control list (ACL) is a table that tells a computer operating system which access rights each user has to a particular system object, such as a file directory or individual file. Each object has a security attribute that identifies its access control list. The list has an entry for each system user with access privileges. Controlling Access to the Kubernetes API | Kubernetes Web09.07.2022 · This page provides an overview of controlling access to the Kubernetes API. Users access the Kubernetes API using kubectl, client libraries, or by making REST requests. Both human users and Kubernetes service accounts can be authorized for API access. When a request reaches the API, it goes through several stages, illustrated in … Security Labels and Mandatory Access Control (MAC) - IBM Mandatory Access Control (MAC) is a security policy that governs which subjects can access which objects, and in what way, based upon certain rules. Label Security | Oracle Oracle Label Security records and enforces access permission for data based on project codes, regions, or data classifications. These controls reduce the risk of unauthorized access to sensitive data and help to demonstrate regulatory compliance. Learn more about Oracle Database security. Watch the overview video (8:16)
Mandatory access control - Wikipedia Access to the labels and control mechanisms are not [citation needed] robustly protected from corruption in protected domain maintained by a kernel. The applications a user runs are combined with the security label at which the user works in the session. Access to information, programs and devices are only weakly controlled [citation needed]. Configure a Security Context for a Pod or Container | Kubernetes Web11.09.2022 · A security context defines privilege and access control settings for a Pod or Container. Security context settings include, but are not limited to: Discretionary Access Control: Permission to access an object, like a file, is based on user ID (UID) and group ID (GID). Security Enhanced Linux (SELinux): Objects are assigned security labels. Sensitivity labels for Microsoft Teams - Microsoft Teams Web21.09.2022 · Control guest access to teams. You can use sensitivity labels to control guest access to your teams. Teams created with a label that doesn't allow guest access are only available to users in your organization. People outside your organization can't be added to the team. Microsoft Teams admin center Security-labels - FHIR v4.3.0 - Health Level Seven International A security label is a concept attached to a resource or bundle that provides specific security metadata about the information it is fixed to. The Access Control decision engine uses the security label together with any provenance resources associated with the resource and other metadata (e.g. the resource type, resource contents, etc.) to
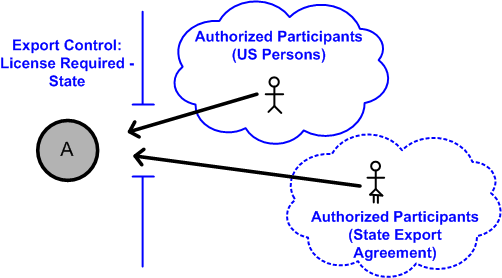
Controlling Access to the Kubernetes API | Kubernetes Jul 09, 2022 · This page provides an overview of controlling access to the Kubernetes API. Users access the Kubernetes API using kubectl, client libraries, or by making REST requests. Both human users and Kubernetes service accounts can be authorized for API access. When a request reaches the API, it goes through several stages, illustrated in the following diagram: Transport security By default, the ... Access Control using Security Labels & Security Clearance - Isode Security Labels and Security Clearance provides a mechanism for controlling access to information that works well for large numbers of users. It can be an effective approach for access control in organizations that do not use non-electronic security labels. The following diagram shows the translation of the earlier example into electronic form. Security Labels and Access Control - Windchill - PTC Support Security labels are applied in addition to standard Windchill access control policy and ad hoc rules. A security label acts as a gate; if the user is not ... Security Labels Overview - PTC Uniquely configured by each site, security labels work with the Windchill access control policies and ad hoc permissions for an object to determine whether a user is authorized to access an object. A site can configure multiple security labels to cover various needs, such as identifying legal information, establishing export control criteria, or protecting proprietary information.
Access Control Security Software - Data Classification | Janusnet Classify and Control · Users can be empowered to manually classify every document they create, assigning an appropriate classification label according to ...
Block Access to Unsanctioned Apps with Microsoft Defender ATP ... Jan 21, 2020 · In Microsoft Defender Security Center under Settings > Advanced features, enable Custom network indicators: Step 3. In the Microsoft Cloud App Security portal under Settings > Microsoft Defender ATP integration, mark the checkbox to enable blocking of endpoint access to cloud apps marked as unsanctioned in Cloud App Security: More info and feedback
Basic roles and permissions | BigQuery | Google Cloud Web26.09.2022 · Basic roles and permissions Overview. BigQuery supports the IAM basic roles for project-level access. Caution: BigQuery's dataset-level basic roles existed prior to the introduction of IAM. We recommend that you minimize the use of basic roles. In production environments, don't grant basic roles unless there is no alternative.
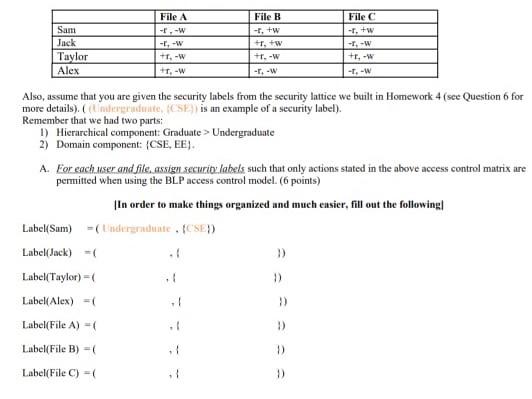
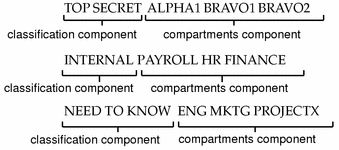
Access Control Models: MAC, DAC, RBAC, & PAM Explained MAC works by applying security labels to resources and individuals. These security labels consist of two elements: Classification and clearance — MAC relies on a classification system (restricted, secret, top-secret, etc.) that describes a resource's sensitivity. Users' security clearances determine what kinds of resources they may access.
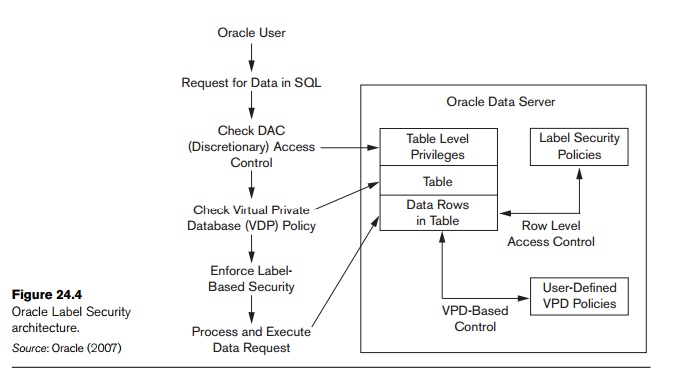
Oracle Label Security Oracle Label Security uses row level data classifications to enforce access controls restricting users to only the data they are allowed to access. It enables organizations to control their operational and storage costs by enabling data with different levels of sensitivity to co-mingle within the same database.
Block Access to Unsanctioned Apps with Microsoft Defender ATP … Web21.01.2020 · By tagging apps in Cloud App Security as unsanctioned based on the comprehensive usage and risk assessment of each app that we provide, those risky app domains are then pushed to Microsoft Defender ATP as custom network indicators in near real-time. This is a single-click control that can significantly improve security posture …
Control external access to resources in Azure Active Directory with ... In this article. Sensitivity labels help you control access to your content in Office 365 applications, and in containers like Microsoft Teams, Microsoft 365 Groups, and SharePoint sites. They can protect your content without hindering your users' collaboration and production abilities. Sensitivity labels allow you to send your organization's content across devices, apps, and services ...
Multi-tenant access for Managed Security Service Providers Web20.07.2020 · Turning on role-based access control will cause users with read-only permissions (for example, users assigned to Azure AD Security reader role) to lose access until they are assigned to a role. Users with admin permissions are automatically assigned the default built-in Microsoft Defender ATP global administrator role with full permissions.
[Knowledge Hub] Windchill PLM Permissions/Access Control/Security Label Article - CS320673 [Knowledge Hub] Windchill PLM Permissions/Access Control/Security Label Modified: 24-Aug-2022 Applies To Windchill PDMLink 10.0 to 12.0 Windchill ProjectLink 10.0 to 12.0 Pro/INTRALINK 8.x + 10.0 to 12.0 Windchill PDM Essentials 10.0 to 12.0 PTC Arbortext Content Manager 10.0 to 12.0 Description How to manage access control?
CS279527 - There is error occurs when loading Security Labels Access ... "modify_security_labels" must have a value from the list "all read modify create delete administrative revise new_view_version change_permissions download modify_content change_domain create_by_move change_context set_state modify_identity
Database Security Requirements Guide - STIG Viewer The DBMS must associate organization-defined types of security labels having organization-defined security label values with information in transmission. Without the association of security labels to information, there is no basis for the DBMS to make security-related access-control decisions. Security labels are abstractions representing the...
Sensitivity labels for Microsoft Teams - Microsoft Teams A team owner can change the sensitivity label and the privacy setting of the team at any time by going to the team, and then click Edit team. Control guest access to teams. You can use sensitivity labels to control guest access to your teams. Teams created with a label that doesn't allow guest access are only available to users in your ...
Access control for folders with IAM | Resource Manager ... Sep 19, 2022 · IAM lets you adopt the security principle of least privilege, so you grant only the necessary access to your resources. IAM lets you control who (users) has what access (roles) to which resources by setting IAM policies. IAM policies grant specific role(s) to a user giving the user certain permissions.
Label-based access control (LBAC) in DB2 LUW | Request PDF Request PDF | Label-based access control (LBAC) in DB2 LUW | data at the row and/or column level based on security labels.
Label-based access control Security labels are objects applied to rows and columns in order to protect these data, and granted to users to give them access to protected data. Protecting tables at row and column levels Protect rows and columns by associating them with security objects by including clauses in the CREATE TABLE and ALTER TABLE statements. Exemptions
Label-based access control in Memgraph - Securing first class graph ... When new labels of yet unseen confidential data are imported into the database, whitelisting ensures they are invisible to all the users and therefore secure until the database administrator grants users with clearance access to the data. You are now familiar with the usage of the label based access control.
Label-based access control (LBAC) overview - IBM In label-based access control (LBAC) a security label is a database object that describes a certain set of security criteria. Security labels are applied to data in order to protect the data. They are granted to users to allow them to access protected data. Format for security label values
Mandatory Access Control: How does it work? - IONOS Web14.10.2020 · Access rights are usually granted by a system administrator and assigned by someone in the company who has sufficient knowledge of the tasks of each user. This ensures that employees can do their jobs without hitting any walls. Implementation and updates are usually carried out automatically by the operating system or a security …
Introduction to column-level access control | BigQuery ... Sep 26, 2022 · Using BigQuery column-level access control, you can create policies that check, at query time, whether a user has proper access. For example, a policy can enforce access checks such as: You must be in group:high-access to see the columns containing TYPE_SSN. To enhance column-level access control, you can optionally use dynamic data masking ...
Security labels - help.hcltechsw.com You can encrypt data, secure connections, control user privileges and access, and audit data security. Security in HCL OneDB™ These topics document methods for keeping your data secure by preventing unauthorized viewing and altering of data or database objects, including how to use the secure-auditing facility of the database server.
Mandatory Access Control Mandatory access control (MAC) is a system-enforced access control mechanism that uses clearances and labels to enforce security policy.
8 Access Control Models - Strengths, Weaknesses, and More Which brings us to our next model of access control - read on. Mandatory Access Control (MAC): the Secure Model Under mandatory access control (MAC), security administrators set access labels for both users and objects. Mandatory access control is the most secure of the major access control models, and also the most demanding to maintain.
LBAC security labels - IBM In label-based access control (LBAC) a security label is a database object that describes a certain set of security criteria. Security labels are applied to ...
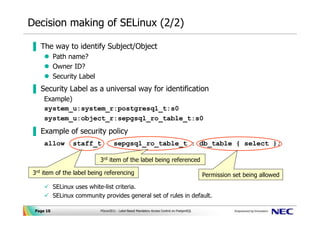
Documentation: 14: SECURITY LABEL - PostgreSQL SECURITY LABEL — define or change a security label applied to an object ... Such systems make all access control decisions based on object labels, ...
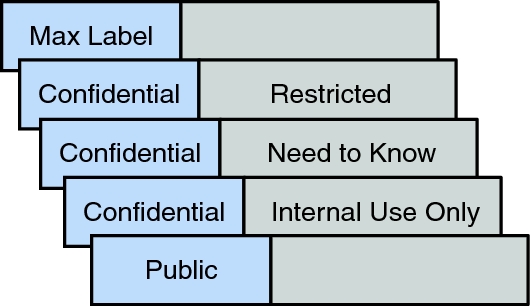
Mandatory Access Control: How It Works - Firewall Times Mandatory access control relies on a system of security labels. Every resource under MAC has a security classification, such as Classified, Secret, and Top Secret. Likewise, every user has one or more security clearances. To access a given resource, the user must have a clearance matching or exceeding the resource's classification.
Access Control List (ACL) - Overview | Consul by HashiCorp Web»Access Control List (ACL) Overview. This topic describes core concepts associated with the optional access control list (ACL) system shipped with Consul. ACLs authenticate requests and authorize access to resources. They also control access to the Consul UI, API, and CLI, as well as secure service-to-service and agent-to-agent communication.
Types of Access Control - Rule-Based vs Role-Based & More - Genea An example of role-based access control is if a bank's security system only gives finance managers but not the janitorial staff access to the vault. ... a system administrator configures access policies and defines security permissions. Labels contain two pieces of information—classification (e.g., "top secret") and category (e.g ...
Setting Access Control Permissions for Agreement Managers - PTC Read permission is required to access any object and view its information page. The following table illustrates additional access control permissions required for actions often completed by an agreement manager. The object location column has the following values. Use these values to determine the domain in which to grant access control ...
Multi-tenant access for Managed Security Service Providers Jul 20, 2020 · Turning on role-based access control will cause users with read-only permissions (for example, users assigned to Azure AD Security reader role) to lose access until they are assigned to a role. Users with admin permissions are automatically assigned the default built-in Microsoft Defender ATP global administrator role with full permissions.
Contact security - Oracle Contact security, also known as Label-Based Access Control (LBAC), allows you to use labels to manage access to contacts in your database. Note: Contact security is part of the Oracle Eloqua Security Administration Cloud Service and is included in the Standard and Enterprise trims.
Security: Access Control - Bosch Security and Safety Systems I Global Getting a connection error when accessing the AEC webpage When trying to access the Access Easy Controller via Microsoft Edge, Chrome or other web browsers, you may get an error, "the connection for this site is not secure", which prevents you from connecting to the AEC. No ratings 427 0 03-30-2022 Can I downgrade my AEC firmware to 2.1.8.5?
Label-Based Access Control - IBM Security labels are objects applied to rows and columns in order to protect these data, and granted to users to give them access to protected data. Protecting ...

Keychain Sticker Card Label Key IC Keychain Access Control EM Keychain Token Portal Reader 13.56MHZ RFID Multi-color Optional
PDF Avery Photo ID Labels for Access Control Cards - Jointech Ent The Market for Labels for Access Control Cards The overall access control market - including software, hardware and consumables - is expected to grow 10-15% annually over the next five years1. HID alone, the largest manufacturer of contactless access control readers & cards for the security industry, has
Introduction to Oracle Label Security Oracle Label Security enables application developers to add label-based access control to their Oracle9iapplications. It mediates access to rows in database tables based on a label contained in the row, and the label and privileges associated with each user session.
Using Security Labels for Directory Access and Replication Control - Isode The access control model is that a Security Label is associated with each entry in the directory, and that label indicates the sensitivity of the information contained in the directory entry. The example DIT "organizations", with different Security Labels.
Which of the following is the access control model (based ... - Skillset This access control system is based on security labeling for security clearances of users and where resources have security labels containing a data ...
Access control - Wikipedia In the fields of physical security and information security, access control (AC) is the selective restriction of access to a place or other resource, while access management describes the process.The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization.. Locks and login credentials are two analogous mechanisms of access control.
How security labels control access - IBM Security labels rely on security label components to store information about the classification of data and about which users have access authority.
Mandatory Access Control - an overview | ScienceDirect Topics Mandatory Access Control ( MAC) is system-enforced access control based on subject's clearance and object's labels. Subjects and objects have clearances and labels, respectively, such as confidential, secret, and top secret. A subject may access an object only if the subject's clearance is equal to or greater than the object's label.
Mandatory Access Control: How does it work? - IONOS Oct 14, 2020 · There are a number of options available for implementing and maintaining access control, including Mandatory Access Control. This model is also used in the political and military branches, which require tamper-proof protection of data. Keep reading to find out how this rule-based access control works and what its pros and cons are.

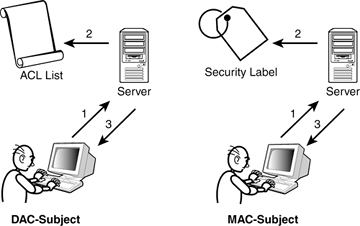

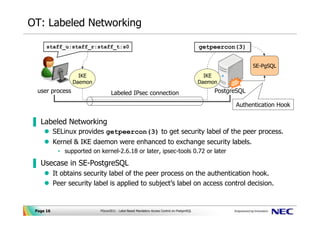

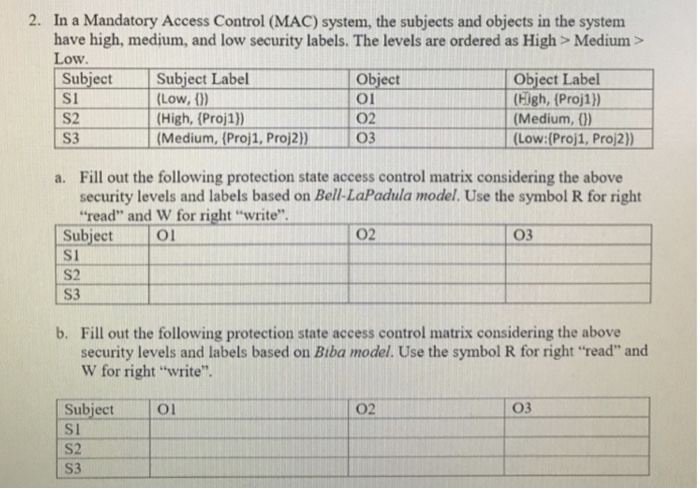















Post a Comment for "42 security labels access control"